Ubuntu plus Haasbot: Step two
Updated (20) 2018
Busy people: skip to "Making modifications"
Please note that while you can do ANY, EVERY or NONE of the suggested modifications, it is VERY important to finish modification you started. Not walking through a single modification to the end might render your server unusable.
Updated (20) 2018
Busy people: skip to "Making modifications"
Foreword
In the previous article, which proven itself worthy, we described how to install Haas trade server on remote server and start it. As many people rightfully pointed, no security configuration were made whatsoever; in this article I will address the issue.Please note that while you can do ANY, EVERY or NONE of the suggested modifications, it is VERY important to finish modification you started. Not walking through a single modification to the end might render your server unusable.
Introduction and disclaimer
Security is a relative term in its nature; and what is "secure" for home use, will not do for commercial company. In this article I am going to address MINIMAL package, which complies with the following:- Easy to install
- Requires zero or almost zero maintenance
- Won't hurt usability
- Require no commercial or out-of-the-repository software
My point here is that security must NOT interfere with the main functionality of the system you are securing; and having some security is better than having none.
If you want to dive in yourself and install industry-grade security for your server feel free to read and use this awesome article from Linode (their guides are pretty good, but I don't like their hosting service), plus throw in an IP filter and trusted VPN (keep in mind VPN and VPS are not the same thing).
Also note that I have no information for the Haas security testing protocol. Once I will know it - I will update the document, either disabling remote IP usage, or highlighting the security used.
Also note that I have no information for the Haas security testing protocol. Once I will know it - I will update the document, either disabling remote IP usage, or highlighting the security used.
Modifications in question
In this section I will give some explanation and reasoning for them being done. If you are eager to just into action skip to the next section.
- Update and upgrade.
Importance: of utter importance
Time: 2-20 minutes
The "update" is the easiest and very safe step to do by far. It should be done whenever update is ready (or automatically even - more of this in later posts); when the "Upgrade" part is a bit tricky. Most often (I'd say 9999 out of 10000 times) this will do good. On the other side, sometimes upgrade can change some internal logic of third-party frameworks\application (for example - Mono), and mess with your software (HaasTradeServer). Another argument against going all-in on upgrade might be the fact that Linux is known to require very little maintenance; also, Ubuntu will not surprise you like other (*cough-cough-Windows*) OS can:
Verdict: "update" and "security upgrade" must be done as soon as possible, for "upgrade" pick up a good moment every month or so and do this too
Bleh :( - Changing ROOT password.
Importance: good to have
Time: 2 minutes
While you might argue that the secure way is to change NOT the password, but actual user allowed to log in through SSH remote user (and you are very true in this saying), I still will point out the compexity of the operation. If you like to change the user, please refer to the article from the "disclaimer" section. The whole point of changing password is just to make sure nobody can get automatically-generated password from your hoster (most probably you received a email with password, username and IP after initial Ubuntu setup). So by changing password you are making sure this email is no longer relevant; however PLEASE remember the new password or write it down in secure place. - Changing default SSH port
Importance: a bonus one; can be skipped
Time: 10 minutes
This move is a bit controversial, and the reasons for the controversy are well-described in this article. However judging by my IT experience it MIGHT prevent future (highly improbable, but still) hack - if your server got into wannabe-hacker list with "open SSH port" remark, there is a small chance that some unexpected future exploit will come out that will allow breaking into SSH, and your server will be exploited. - Changing default HTS port
Importance: a bonus one; can be skipped
Time: 10 minutes
This move basically mirrors previous one, but for HTS itself. Right now HTS is using rare custom port, and hackers community completely unaware of the product. However I give 6~10 months untill unformation will spread, and HTS server hack will become a thing. So to be ready for that the least we can do is to move from well-known port. - Setting up firewall
Importance: utterly important
Time: 2 minutes
Every Linux comes with a pre-installed firewall (called iptables), but most usually it is deactivated by default. While Linux is better designed in terms of network performance than Windows, it is still important to configure firewall. I will use the UFW - Uncomplicated FireWall product - which is, in fact, NOT a firewall, but just a "command interface" for default Linux firewall. - Fail2ban security program
Importance: good to have
Time: 5 minutes
This program will ban IP of a user trying incorrect password too many times. Really good program, with a lot of options, which are desribed in good details here. However we will go with easy default set up.
Making modifications
Step 0: insurance.
To protect you from yourself please take these precautions first:
- Back up your HTS config\bots\keys\etc as described in this article
- Make an actual note (text file or a paper notepad) and write down there the following information:
Server IP address
Server SSH port (default:22, write new one if you decide to change it)
Root password (write both old one and new one if you decide to change it)
Server HTS ports (defaults are 8090 and 8092; write down new ones if you decide to change it)
Please, DO do it.
- Update and upgrade
If you log in to your server and see message about packages that can be "updated" - it's a no brainer.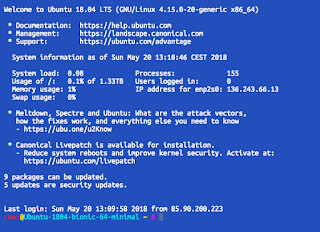
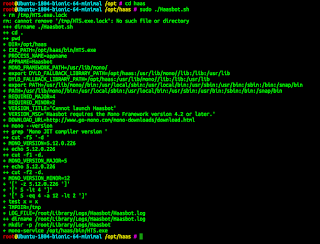
Just fire up the command and see what's in there for you:
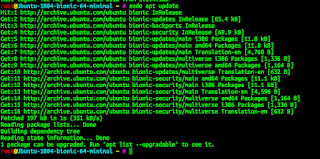
sudo apt update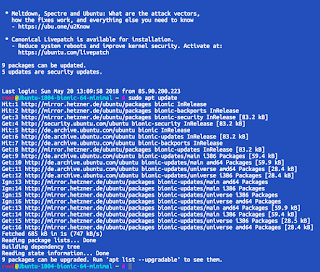
Now we see that a lot of packages need "upgrading"; let's do just that:
sudo apt upgrade
This may or may not take some time:
Please note that while NOT required, it surely is a good idea to also restart HaasBot afterwards:
sudo killall monothen
cd /opt/haasand finally
sudo ./Haasbot.sh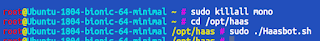
- Changing Root password
To do that simply execute:
passwd
Enter new password and confirm. NOTICE: that input is NOT reflected in terminal for security reasons. No asterisks, no actual letters. No feedback at all, which might be confusing.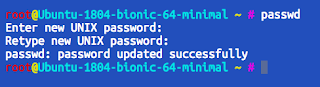
You can paste password, too, for example your password-manager-generated one.
I HIGHLY recommend using VERY-VERY secure password, as it's the first line of defense. If you can't think of one - feel free to use special service like LastPass or any other resource
Write down new pass to your "insurance" note. - Changing default SSH port - PROCEED WITH EXTREME CAUTION
This step will make your server invisible for the 99% of wannabe-hackers and "Mr. Robot" fans (this is a decent and valid TV show in terms of actual hacking representation, by the way)
BE WARNED: if you mess up any of the steps most probably server will be locked out forever and will need a complete re-install. So, being careful, type the command to edit SSH daemon config:
nano /etc/ssh/sshd_config
to open the config file
This will open nano editor, which should be used to locate #Port 22 line and remove # sign as well as changing number to something else, from range 1024 - 65535 while trying to avoid "privileged" or "cool" number like 2222 or 3333 or 4242 or something like that. Script kidos are using pre-configured port scanners, and scan port 22 for vulnerabilities; advanced kids also scan "cool" ports. So picking 8923 is a better idea than 1337 Other than that actual number does not matter.
WARNING: Port can NOT coincide with other taken port. So far HTS is using 8090 and 8092, so keep away from those.
Initial version: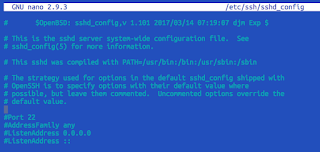
What we need to have (use your port number instead of 4022)
Then press Ctrl+X followed by Y and then Enter. After that it's time to restart the SSH daemon and reconnect by running the command
service sshd restart
which should not give any output; after that we need to exit the connection and re-configure Termius by running
exit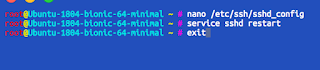
If everything was done correctly, server becomes unreachable from Termius for now
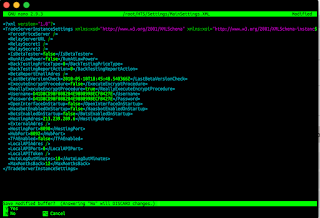
To fix that we need to "edit" host settings and change "port" to the value we've chosen - IMPORTANT - remember to DELETE default value "22" in the field first.
NONE-TERMIUS USE: if you use other tools (putty, console, issh or else) you will need to change port, too. If there is no additional field for port just use IP:PORT syntax. Example for my server will be 136.243.66.13:4022 instead of just 136.243.66.13
My choice of 4022 port is not fitting beautifully, but works just fine. Save, reconnect and you might need to re-accept server fingerprint
Write down new port to your "insurance" note. - Changing HTS default port
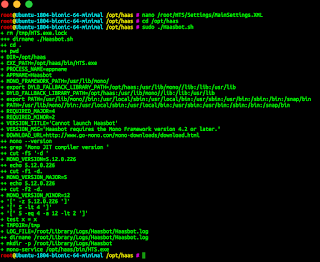
Back to basics! Changing HTS config once more. Easy-peasy, just run:
nano /root/HTS/Settings/MainSettings.XMLAnd now go and change <HostingPort> and <HubPort> values. Same drill as with SSH port - pick any ports from range 1024 - 65535 while trying to avoid "privileged" or "cool" number like 2222 or 3333 or 4242 or something like that.
WARNING: no port can coincide with any other taken port. If you changed SSH port - you can't use same value for HTS.
Once you pick new numbers (in my example I've picked 48090 and 48092) and wrote them into editor do old trick: Press CTRL+X followed by Y followed by ENTER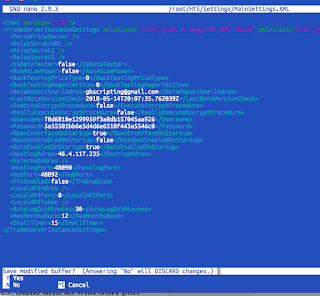
Then go and restart HTS
sudo killall mono
then
cd /opt/haasand finally
sudo ./Haasbot.sh
Now write new ports down into your "insurance" note - Firewall control - UFW - PROCEED WITH EXTREME CAUTION
For the obsolete versions of Ubuntu (16, 17) you might need to use sudo apt install ufw command.
This modification requires your "insurance" note information. Inability to use correct ports in this step will lock your server out forever and require complete reinstall.
Our Firewall will allow only HTS and SSH connections, and disable every single other one.
The number in the following command is YOUR SSH PORT from the "insurance" note. If your SSH port were not modified then use port 22; otherwise use the number of new SSH port from your "insurance" note.
I have changed mine to 4022, so the command for me is:
sudo ufw limit 4022
using "limit" here will not allow to generate too many connections. As I use only one connection at a time, it might help with security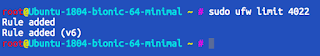
Then we need to allow our HTS ports to work (again, consult with your "insurance" note for the correct ports) - I have changed mine from 8090 to 48090, so the commands are
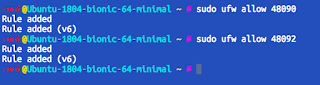
sudo ufw allow 48090
and
sudo ufw allow 48092
now only two last steps left We need to disable every other possible connectivity now by default with:
sudo ufw default deny incoming And finally enable firewall
sudo ufw enable
and then press Y and Enter
To make it start.
If your server is still accessible and HTS works - you are doing everything just as required =) - Fail2ban
The last for today - installing Fail2ban to ban those who fail to log in many times in order to prevent password bruteforce attack. Simply type
sudo apt install fail2ban
and then press Y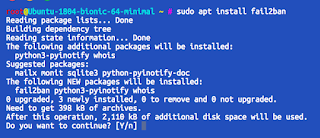
After really small and fast download program will automatically install and start
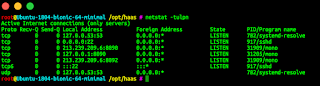
You can check it is working by running:
fail2ban-client status
Answer about number of jails indicate succesfull run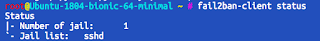
Please be safe, ask questions and comment on what's not clear in this post!